CS GATE 2017 PAPER 01 - Online Test
Q1. Consider the following intermediate program in three address code
p = a - b
q = p *c
p = u * v
q = p + q
Which one of the following corresponds to a static single assignment form of the above code
?
Answer : Option B
Explaination / Solution:
No Explaination.
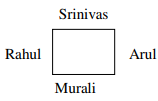
Q2. Rahul Murali, Srinivas and Arul are seated around a square table. Rahul is sitting to the left of
Murali. Srinivas is sitting to the right of Arul. Which of the following pairs are seated
opposite each other ?
Answer : Option C
Explaination / Solution:

Q3. “The hold of the nationalist imagination on our colonial past is such that anything
inadequately or improperly nationalist is just not history”
Which of the following statements best reflects the author’s opinion ?
Answer : Option B
Explaination / Solution:
No Explaination.
Q4. Consider the following table:
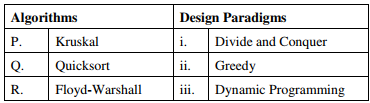

Match the algorithms to the design paradigms they are based on.
Answer : Option C
Explaination / Solution:
Kruskal’s algorithm follows greedy approach in order to find MST of a connected graph.
Quick sort follows divide and conquer strategy. Floyd Warshal algorithm is used to find the
shortest path between every pair of vertices and it follows dynamic programming strategy.
Q5. Consider a combination of T and D flip-flops connected as shown below. The output of the D flip-flops is connected to the input of the T flip-flop and the output of the T Flip-flop connected to the input of the D Flip-flop. 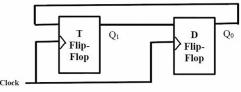

Initially, both Q0 and Q1 are set to 1 ( before the 1st clock cycle). The outputs
Answer : Option B
Explaination / Solution:

Q6. Consider the C functions foo and bar given below:
int foo (int val ) {
int x = 0;
while (val > 0) {
x = x + foo ( val --);
}
return val ;
}
int bar (int val ) {
int x = 0;
while (val > 0) {
x = x + bar (val – 1) ;
}
return val ;
}
Invocations of foo (3) and bar (3) will result in:
Answer : Option B
Explaination / Solution:
Foo (3) calls foo (3) which in turn calls foo(3). This goes on infinite number of times which
causes memory overflow and causes abnormal termination.
Bar(3) → bar (2) →bar (1) →bar (0) (return 0) from here onwards bar (1) will call bar (0)
and bar (0) will return 0 to bar (1) & this goes on forever without causing memory overflow.
Q7. Consider the following two functions.
void funl (int n) { void fun2 (int n) {
if (n = =0 ) return; if (n = = 0) return ;
printf (“%d” , n); printf (“%d” , n);
fun2 (n - 2); fun1(++n) ;
printf (“%d” , n); printf (“%d” , n);
} }
The output printed when fun1 (5) is called is
Answer : Option A
Explaination / Solution:
In this the fun1() is calling fun2() after printing value and after returning from fun2(),it prints
the same value. In the fun2() also the same thing happens So by looking options we can judge
the correct sequence of output.
Q8. A sender S sends a message m to receiver R, which is digitally signed by S with its
private key. In this scenario, one or more of the following security violations can take
place.
I. S can launch a birthday attack to replace m with a fraudulent message.
II. A third party attacker can launch a birthday attack to replace m with a fraudulent
message.
III. R can launch a birthday attack to replace m with a fraudulent message.
Which of the following are possible security violations?
Answer : Option B
Explaination / Solution:
Sender can launch a Birthday Attack to replace with fraudulent message, because he has the
signature and he can decrypt the signature by his own public key and gets the hash value.
With that same hash value, he can create another message and can be sent instead of original.
Hence option(B) is correct.
Q9. When two 8-bit numbers A7....A0 and B7.....B0 in 2’s complement representation (with A0 and B0 as the least significant bits ) are added using a ripple-carry adder, the sum bits
obtained are S7….S0 and the carry bits are C7….C0. An overflow is said to have occurred if
Answer : Option C
Explaination / Solution:
Overflow flag indicates an over flow condition for a signed operation. Some points to
remember in a signed operation:
* MSB is always reserved to indicate sign of the number.
* Negative numbers are represented in 2’s – complement.
* An overflow results in invalid operation.
2's complement overflow rules:
* If the sum of two positive numbers yields a negative result, the sum has- overflowed.
* If the sum of two negative number yields a positive result, the sum has overflowed.
* Otherwise, the sum has not overflowed.
Overflow for signed numbers occurs when the carry-in into the MSB (most significant bit) is
not equal to carry-out. Conveniently, an XOR-operation on these two bits can quickly
determine if an overflow condition exists.
Q10. Consider a TCP client and a TCP server running on two different machines. After completing
data transfer, the TCP client calls close to terminate the connectional and a FIN segment is
sent to the TCP server. Server-side TCP responds by sending an ACK which is received by
the client-side TCP. As per the TCP connections state diagram (RFC 793), in which state does
the client-side TCP connection wait for the FIN from the sever-side TCP?
Answer : Option D
Explaination / Solution:
No Explaination.