CS GATE 2010 - Online Test
Q1. What is the appropriate pairing of items in the two columns listing various
activities encountered in a software li fe cycle?
P. Requirements Capture 1. Module Development and Integration
Q. Design 2. Domain Analysis
R. Implementation 3. Structural and Behavioral Modeling
S. Maintenance 4. Performance Tuning
Answer : Option B
Explaination / Solution:
No Explaination.
Q2. The program below uses six temporary variables a, b, c, d, e, f.
a = 1
b = 10
c = 20
d = a + b
e = c + d
f = c + e
b = c + e
e = b + f
d = 5 + e
return d + f
Assuming that all operations take their operands from registers, what is the
minimum number of registers needed to execute thi s program without spilling?
Answer : Option C
Explaination / Solution:
No Explaination.
Q3. Consider the following schedule for transactions T1, T2 and T3:
T1 T2 T3
Read(X)
Read(Y)
Read(Y)
Write(Y)
Write(X)
Write(X)
Read(X)
Write(X)
Which one of the schedules below is the correct serialization of the above?
Answer : Option B
Explaination / Solution:
No Explaination.
Q4. A system has n resources R0,…,Rn-1, and k processes P0,…..Pk-1. The
implementation of the resource request logic of each process Pi. is as follows:
if (i% 2==0) {
if (i<n) request Ri;
if (i+2<n)request Ri+2 ;
}
else {
if (i<n) request Rn-i ;
if (i+2<n)request Rn-i-2 ;
}
In which one of the following situations is a deadlock possible?
Answer : Option B
Explaination / Solution:
No Explaination.
Q5. The following program consists of 3 concurrent processes and 3 binary
semaphores. The semaphores are initialized as S0=1, S1=0, S2=0.
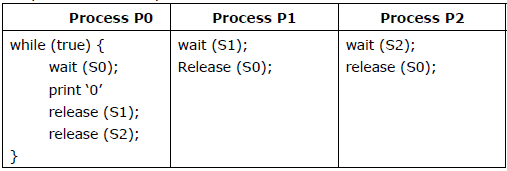

How many times will process P0 print ‘0’?
Answer : Option D
Explaination / Solution:
No Explaination.
Q6. Suppose computers A and B have IP addresses 10.105.1.113 and 10.105.1.91
respectively and they both use the same net mask N. Which of the values of N
given below should not be used if A and B should belong to the same network?
Answer : Option C
Explaination / Solution:
No Explaination.
Q7. A computer system has an L1 cache, an L2 cache, and a main memory unit
connected as shown below. The block size in L1 cache is 4 words. The block size
in L2 cache is 16 words. The memory access times are 2 nanoseconds.
20 nanoseconds and 200 nanoseconds for L1 cache, L2 cache and main memory
unit respectively.
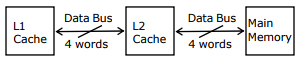

When there is a miss in L1 cache and a hit in L2 cache, a block is transferred
from L2 cache to L1 cache. What is the time taken for this transfer?
Answer : Option D
Explaination / Solution:
No Explaination.
Q8. Consider a network with 6 routers R1 to R6 connected with links having
weights as shown in the following diagram
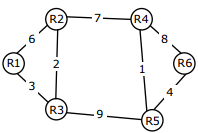

All the routers use the distance vector based routing algorithm to update their
routing tables. Each router starts with its routing table initialized to contain an
entry for each neighbour with the weight of the respective connecting link.
After all the routing tables stabilize, how many links in the network will never
be used for carrying any data?
Answer : Option C
Explaination / Solution:
No Explaination.
Q9. A computer system has an L1 cache, an L2 cache, and a main memory unit
connected as shown below. The block size in L1 cache is 4 words. The block size
in L2 cache is 16 words. The memory access times are 2 nanoseconds.
20 nanoseconds and 200 nanoseconds for L1 cache, L2 cache and main memory
unit respectively.
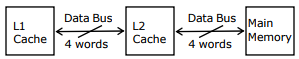

When there is a miss in both L1 cache and L2 cache, first a block is transferred
from main memory to L2 cache, and then a block is transferred from L2 cache to
L1 cache. What is the total time taken for these transfers?
Answer : Option B
Explaination / Solution:
No Explaination.
Q10. Consider a network with 6 routers R1 to R6 connected with links having
weights as shown in the following diagram
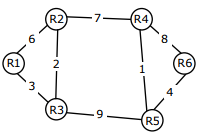

Suppose the weights of all unused links in the previous question are changed
to 2 and the distance vector algorithm is used again until all routing tables
stabilize. How many links will now remain unused?
Answer : Option C
Explaination / Solution:
No Explaination.